Exploit:Java/Blacole Exploit Kit
by Aderito
(Germany)
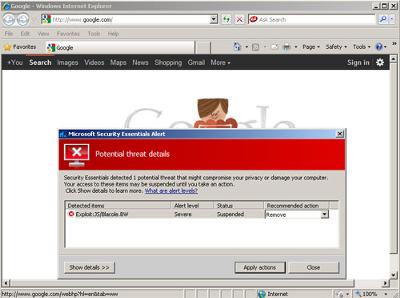
Exploit:Java/Blacole.BW Google False-Positive
Microsoft Security Essentials detected and removed the Exploit:Java/Barcole infection from my computer.
My understanding is this Trojan is a Black hole Exploit Kit detection component. These kits are used by hackers to distribute their Malware, ranging from targeted advertisements to key loggers.
Microsoft Security Essentials classes the Alert Level as Severe. This means the exploit is widespread or exceptionally malicious, and should be removed immediately.
It also has no symptoms, i.e. no impact on your computer's performance and no error messages. It buries itself in your computer system to avoid anti-virus detection.
It gets onto your computer from a compromised Web Server you have visited. The cyber-criminal installs the kit onto the Web Server.
If you visit this Server and your computer has the right vulnerabilities, the rootkit activates and exploits by downloading malware on to your machine.
The vulnerability in my case is with Sun Java. I should really update it to the latest version, so this doesn't happen again.
Thanks Adertio for contributing. I've added further comments in the comments section.
This is an example of a False-Positive detection as a result of a faulty Valentine's Day Security Update.
Microsoft Security Essentials flagged this Java Exploit when home computer users visited google.com – the world's most visited website!
Google is not infected with the Blacole Trojan. Through my research it looks like if you clicked the remove option in these circumstances then no new problems are triggered on your computer.
It is likely MSE would tell you that it could not detect the threat (because there is no threat to start with!).
Microsoft rectified this issue by quickly releasing a further virus definition update.
In my experience, a faulty patch or definition file is released a couple of times a year. They can be a pain to Business users and their IT Support Departments, but they are usually corrected quickly by the vendor.
Comments for Exploit:Java/Blacole Exploit Kit
|
||
|
||
- Home
- Computer-help
- Exploit:Java/Blacole Exploit Kit
