WannaCry Ransomware Attack Explained
The wannacry ransomware attack of May 12th 2017 was devastating for many organizations and institutions around the world.
It was the largest cyber-attack in history, with over 150 Countries affected, and hundreds of thousands of computers performing a variety of tasks, from banking to medical devices.
Here we explain how this particular attack worked, and what could have been done to prevent it.
Join The Human Byte — Get The Ultimate BIOS Update Guide
- Receive the Ultimate BIOS Update Pack
- Includes a set of checklists, flowcharts, and your Beep Code Finder support your BIOS update process
- Also includes a full set of eBooks including a Survival Guide and step-by-step Support Guide
- Receive regular emails with practical information you can use
- I only use your e-mail for the newsletter. Unsubscribe anytime.

WannaCry Ransomware Attack | What is Ransomware?
Ransomware is a form of malware that extorts money from victims by encrypting their data files. It does not discriminate between which files are locked away (encrypted), so at best you lose access to something meaningless, or at worst, your very sensitive information such as medical records.
To release or decrypt the data files, the victim is ordered to pay a ransom. The ransom demanded is usually in Bitcoin currency.
Bitcoin is a decentralized digital currency with no central bank. It is an attractive method of payment for cyber criminals because of the difficulty authorities have in tracing who is collecting the victim’s ransom payments on the Dark Web.
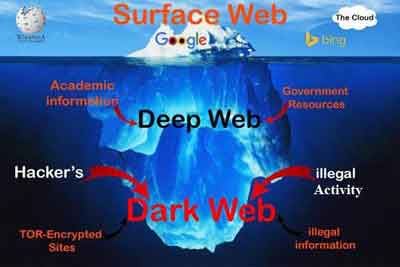 World Wide Web Breakdown
World Wide Web BreakdownThe dark web has gained notoriety as a place where lots of illegal activity takes place. It's only accessible via the ToR browser (The Onion Ring).
The visible internet that is accessible via Google and other search engines is approximately 4% of the World Wide Web.
There is currently no legislature to protect you from crimes that take place of the dark web, and there is no doubt the origins of the wannacry ransomware attack started here!
If you decide to use the ToR browser, I would suggest you use a good VPN solution, a machine with no personal information and public internet access.
How WannaCry Works
The wannacry ransomware attack is classed as a zero-day attack. This means antivirus companies were unaware of the malware and were unable to detect and remove until after the damage was already done.
There are two parts to this ransomware - the worm (propagation) and the ransom (payment):-
- The worm is jargon for a virus’s ability to copy itself on to other vulnerable computers. This imitates the biological virus infection process;
- The ransom is the part that locks your files and demands a payment to unlock them.
The WannaCry worm element checks computers for a vulnerability or flaw in SMB, or the Service Messaging Block.
SMB is a method of communication that enables computers to talk to shared file locations and shared devices, such as. The means of communication is called a Port. SMB uses port number 445.
A computer that has the flaw is then exploited by EternalBlue. This is a method developed to fool a computer into accepting the worm’s computer code.
WannaCry's computer code included a backdoor tool called a DoublePulsar. A backdoor tool is a means of bypassing a computer's security mechanism.
The DoublePulsar ultimately enables the Ransom part of the virus to be loaded and facilitates further attacks from criminals to re-infect machines with their Ransomware variants.
The Shadow Brokers APT (Advanced Persistent Threat) group are alleged to have obtained EternalBlue and DoublePulsar from the National Security Agency (NSA) by hacking their systems.
The NSA is a governing body responsible for global monitoring, collecting and processing information and data for foreign intelligence and counter-intelligence purposes.
Many believe the security patch made available by Microsoft to protect machines against the WannaCry Ransomware attack was made possible by the NSA warning Microsoft about the security flaw.
There are ongoing discussions between the NSA, Microsoft and other stakeholders about the 'stockpiling of software flaws’ by Government agencies for tactical cyber warfare advantage.
A combination of the flaw, the exploit, and the tool enabled WannaCry to move through across the world, infecting other vulnerable machines and encrypting data.
Users do not notice anything is wrong until the Ransomware message appears on-screen.
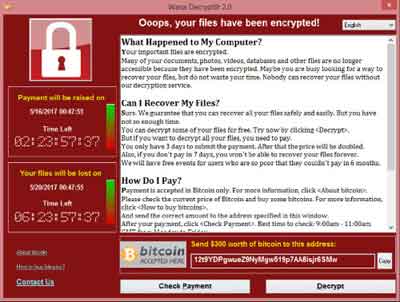 WannaCry Ransom Payload Screen
WannaCry Ransom Payload ScreenRansomware cyber criminals are under no obligation to unlock your files even if the ransom is paid, and even if they are unlocked, there is no guarantee the files will not be corrupted. Never pay the ransom!
Fortunately, a Cybersecurity expert called ‘MalwareTech’ identified and enabled a Kill Switch for WannaCry.
This was done by registering a web address that triggers the WannaCry payload into shutting down as this triggers interrogation conditions typically used by IT security experts, this stopping the wannacry ransomware attack from spreading.
Kill Switches do not prevent an infected machine from encrypting, but to prevent other machines that are vulnerable to infection, assuming these machines can ‘see’ the web address.
Cyber Criminals tried to take the Kill Switch down using an approach called a Botnet attack.
A Botnet attack is where hackers find a way to covertly take over many computers and co-ordinate them to attack a particular target and make it unavailable.
They do this by bombarding the target with spam data, so it cannot cope with the demands placed upon it.
The method used by the ‘conscripted’ machines is called a Distributed Denial of Service attack (DDoS).
If the Cyber Criminals were to be successful, there is a risk of the WannaCry Ransomware resuming and infecting more machines.
Microsoft released a security patch for the SMB flaw on the 14th March 2017. However, this only applied to supported Operating Systems.
Microsoft took the unusual step of releasing out of bound patches for legacy operating systems such as Widows XP. These were made available 24–36 hours after the WannaCry ransomware attack started to gain traction across the mainstream media.
If organizations across the globe, such as Telefonica in Spain, Car Manufacturers and even the Russian Interior Ministry, had applied the patch successfully on supported operating systems when it was released by Microsoft, the overall impact of WannaCry would have been negligible.
Instead, organizations lost money, consumers lost data, and the IT industry wasted a lot of time recovering from this, just to get back to where they were on Thursday 11th May 2017.
WannaCry Ransomware Attack | Final Thoughts
Modern ransomware attacks are sophisticated and the frequency in which they are being created and released is increasing. Within a few days of the WannaCry attack, two variants were
released by hackers.
There are estimated to be at least 4000 ransomware attacks taking place each day somewhere
across the world, and over 18 million types of ransomware existing.
Antivirus suppliers can't identify and prevent infection from all types of virus or malware. Microsoft can't identify and write security patches for all flaws in their software.
In addition, if the NSA and other government agencies are unable to trace or catch the perpetrators of such attacks, then we are all subject to increased risk, especially in the era of Big Data and the Internet of Things (IoT).
WannaCry locked data and extort money from victims. However, ransomware can also be written to steal data and send it to the criminals, who can subsequently release it in the public domain if the ransom is not paid.
There is clearly a growing threat. Ransomware sophistication is set to increase, and with more devices being connected to the Internet, the risk of a re-occurrence and subsequent impact is higher than ever.
The next Ransomware attack could strike at any time, and be more devastating than WannaCry. You have been warned!