The Relationship Between Cyber Security and Identity Theft
Cyber security and identity theft go together, especially since this long-standing activity moved on to the Internet.
Most of us are now aware of the need for good antivirus software and to ensure our software is patched. However, without enabling additional cyber security features such as multifactor authentication, one of the consequences could be the theft of your identity, then fraudulent activity undertaken in your name.
In the UK, the numbers suggest the average household has up to 8 internet-connected devices, from desktop computers, to tablets and mobiles. 95% of Britons buy goods and services online. I expect similar figures across most of the first world.
It is this level of connectivity and interaction we have online that makes us more vulnerable to cyber criminal activity than ever before, and online ID theft is on the rise.
There are demographics that show which age ranges are most likely to fall for such scams. However, my personal view is that we are all vulnerable, regardless of our age.
With this in mind, the article that follows ultimately describes how to protect yourself from identity theft. We look at what ID theft is, and how the subsequent fraudulent activity is committed.
We then look at ways to prevent identify theft and how to report it if it happens to you.
Join The Human Byte — Get The Ultimate BIOS Update Guide
- Receive the Ultimate BIOS Update Pack
- Includes a set of checklists, flowcharts, and your Beep Code Finder support your BIOS update process
- Also includes a full set of eBooks including a Survival Guide and step-by-step Support Guide
- Receive regular emails with practical information you can use
- I only use your e-mail for the newsletter. Unsubscribe anytime.

What Is Identity Theft?
Identity theft can be defined as when a (cyber) criminal illegally represents themselves as you (online) for financial gain.
It is usually about the money with cyber criminals and this is their motivation for stealing your (and your families) name, address, birthdate, National Insurance or Social Security number, photographs from your social media accounts and if accessible, details from your utility companies.
Other personal identifiable information such as drivers licences can also prove valuable to cyber criminals.
Each piece of information acquired is a valuable piece of the jigsaw for the cyber criminal to commit identity fraud. This can include emptying your bank and investment accounts, taking our credit cards, pay day loans and store cards, all in your name.
In some extreme circumstances, your details could be given to the police if the perpetrator is arrested.
Identity theft and fraud is on the rise due to our increased online presence and interactions, especially social media platforms.
In addition, all of our personal information held by online companies are subject to data breaches, as we have seen in the past, and will do again in the future.
The Equifax credit reporting company data breach in September 2017 leaked personal information for over 147 million people, including social security numbers, dates of birth, credit card numbers and drivers licences.
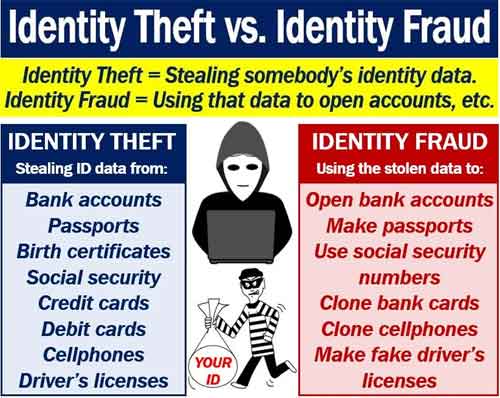 Cyber Security and Identity Theft
Cyber Security and Identity TheftIdentity Theft versus Identity Fraud
Source:- marketbusinessnews.com
There are signs to look out for that could indicate you have been subject to ID theft. This includes unusual expenses appearing on your credit card statements, and your credit score nosediving.
Anti-fraud and suspicious activity systems are excellent these days. If large amounts of money is withdrawn or if login attempts take place from other parts of the world, anti-fraud systems will notify you or freeze your account until you take decisive action to resolve,
Below is an image from an e-mail I received a few years ago about suspicious activity on the Pinterest account.
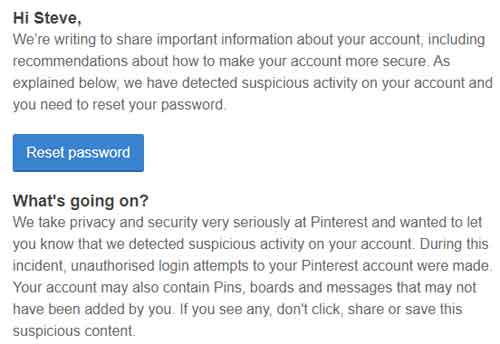 Cyber Security and Identity Theft
Cyber Security and Identity TheftSuspicious Activity Alert I Received From Pinterest A Few Years Ago
Online identity fraud can also involve your children. There are horror stories where ID theft has affected children as they grow up and are at an age where they can apply for college loans, buy their first car or start their first job.
If you hear the term synthetic identity theft, it is just a way of describing how the cyber criminals use a combination of different people's personal information to carry out fraudulent activity.
This could your child's social security number (that is not registered yet), or even a number that hasn't yet been assigned, combined with the postal address of another home (usually with a good credit rating), and other people's personal information.
In the US, Tax and Medical ID fraud is rampant. This is where the cyber criminals acquire your details to file a fraudulent tax return to them, or receive medical care, on your dime.
How Is Identity Theft Committed?
How does identity theft happen exactly? Well, one of the common mediums for conducting ID theft is over public Wi-Fi. These free services are not always secure, and could have cyber criminals recording all activity taking place, including how you access your back accounts or credit card details when paying for online purchases.
If you are using a public Wi-Fi service, do not enter any personal information, such as login details. Furthermore, subscribe to a good VPN service for added protection.
How many accounts have you set up in your lifetime? How many do you still use? What happened to the accounts that have been disbanded or forgotten about?
There is every chance the majority of these accounts still exist and retain all the information you entered, including home addresses, e-mail addresses and passwords.
This is why it is critical you monitor new and other correspondence about any form of company data breach, and then take quick, decisive action when they occur, i.e. at least change your password and if possible, close the account down.
Phishing scams are another attack vector to be aware of, especially by e-mail. This is where the fraudsters obtain your account information by diverting you to their website which is set up to look like a legitimate site, and where you unwittingly enter your details and effectively hand over the keys to the castle to the fraudsters.
Also avoid opening that e-mail attachment from someone you don't know, or even from someone you do know, but the context or language of their e-mail doesn't make sense e.g. writing style, language, e-mail subject heading etc. If in doubt, delete before opening.
This also applies to the “You've won a competition” e-mails (that you've never entered) and seasonal correspondence. It is tempting to click that link for the once-in-a-lifetime exclusive Black Friday deal on the latest games console.
Is it, though? How many others received the same offer? (Millions, is the answer, which doesn't make it such an exclusive offer in the first place, does it!).
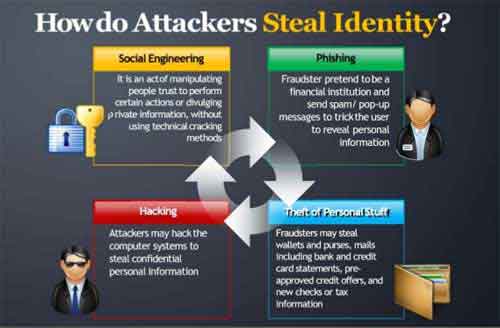 Cyber Security and Identity Theft
Cyber Security and Identity TheftHow Do Attackers Steal Identity?
With criminal identity theft on the rise, it should come as no surprise to leant that fraudulent schemes are becoming more intricate and elaborate. This also includes long-term scams using social media, such as the case of 'Alexandre Nikolov'.
In Bulgaria, Spas Visilva stole Alexandre Marinez' identity, including his personal details and social media photographs. Visilva used this information to fraudulently create multiple fake online accounts under the pseudonym Alexandre Nikolov.
Over a 5-year period, the Alexandre Nokolov Pseudonym became very well known in Bulgaria. Carefully choreographed by Visilva, 'Alexandre Nikolov' was appointed to top jobs in multinational corporations and high-paying consultancy roles. He also gathered a large online following, including national journalists and politicians.
Once his following was fully established, Visilva set up a Ponzi scheme, offering discounted flights on Facebook, using his established connections with the airline industry.
A Ponzi scheme is where the fraudster sets up a scheme that promises, and delivers, good financial returns for early investors, by using the latest investor's money to 'pay out' (minus a cut for the fraudster).
No business activity actually takes place. The fraudster makes a lot of money from the scam, and eventually the newest investors lose all of their money as the number of new investors decrease and fizzle out.
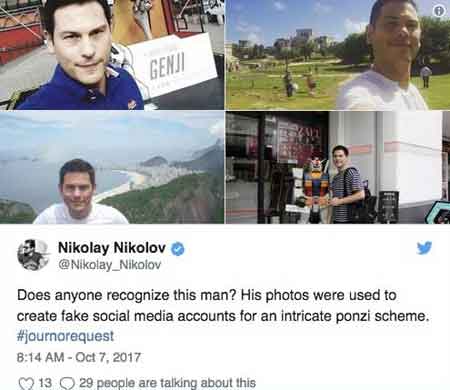 Cyber Security and Identity Theft
Cyber Security and Identity TheftAlexandre Nikolov Online Ponzi Scheme Fraud
Source:- social-engineer.org
When the money started to dry up and new buyers didn't receive their airline tickets, Nicolay Nikolov, a journalist who was invited into the exclusive Facebook group for the discounted flight scam, started investigating, which eventually ended up with Visilva's arrest.
This is an extreme case of cyber security and identity theft, but I expect this type of elaborate scheme or scam to become more common as cyber criminals refine their techniques and technology advances.
How To Prevent Identity Theft And Report
There is no silver bullet in preventing identity theft and the fraud that follows. To a certain extent, we are reliant on our online providers to inform us in a timely manner when they suffer a cyber security and identity theft event.
However, there are some proactive steps you can take to keep yourself safe online, and avoid cyber security and identity theft events in the future.
For example, you could freeze your credit accounts, so they cannot so easily be exploited. It is free to do so, (albeit a bit of a pain), but relatively straightforward to unlock when you need to open a new bank account, for example.
Also keep your National Insurance/Social Security Number safe. Don't carry around with you and shred any printed documentation. It is good practice to shred any documentation you are discarding.
Have a look at the video below from the UK. It is over 9 years old, but is still just as relevant today. Take the shredding of documentation seriously.
The ID Theft Hustle Video
If you receive an e-mail asking for such information, ignore or at least question why before disclosing.
Furthermore, take a moment to understand how Phishing and website spoofing works. The e-mail below from the Federal Trade Commission (FTC) looks genuine.
However, have a look at where the web link is sending you. That doesn't look like a legitimate FTC web address, does it?
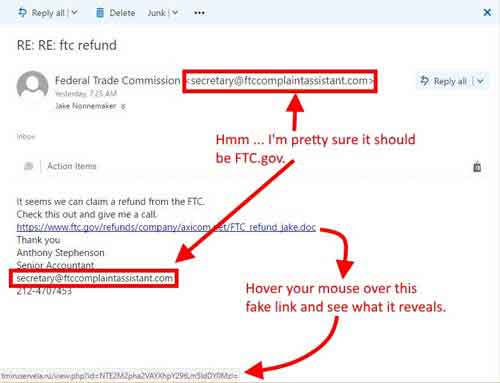 Cyber Security and Identity theft
Cyber Security and Identity theftPhishing E-Mail Scam Example
Source:- axicom.net
Always question phone calls from banks and government contacts that ask you for password and other information that could compromise your online accounts. Return their call using a different mobile or landline, using the entities known number.
You never know whether that call is costing you premium rates, or whether there is a trace on your line where your callback is re-routed in to the scanners 'call centre'.
Secure passwords or passphrases are a must, alongside two-factor or multifactor authentication when available. Similarly, take the time to set up alerts, such as when credit and debit cards are used, or when a spending total has been breached, or when withdrawals over a specified amount occur.
Consider opening a Digital Wallet. This is where credit and debit card information is held in an encrypted app, or wallet, and can be used to pay for goods and services online or even contactless in department stores.
It is a one-stop shop for all your banking details such as PINs, and coupled with MFA, can provide a very secure location for your personal information.
Now you have an understanding of how to avoid identity theft, how do you report it if it happens to you?
In the US, you can report identity theft to the FBI, or report any suspicious activity to the Federal trade commission. Make sure those who are suspected on this heinous crime are brought to justice, like this one below.
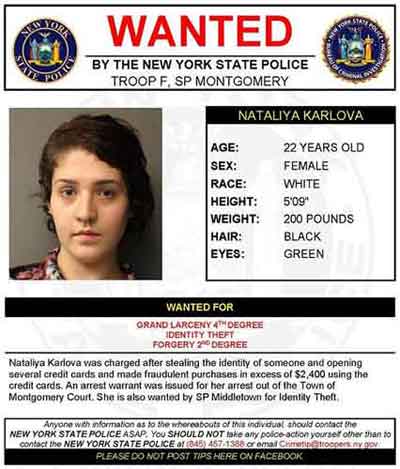 Cyber Security and Identity Theft
Cyber Security and Identity TheftWanted Poster For An Alleged Fraudster
Source:- hudsonvalleycountry.com
In the UK, you can report any suspicious activity to Action Fraud.
Cyber Security and Identity Theft | Final Thoughts
Cyber security and identity theft don't always go together. Those hell-bent on identify theft can come up with some interesting methods for acquiring your information, including dumpster/bin diving and tombstone theft.
At my local refuse or tip centre, the workers there know the 'divers' by name as they wait outside the perimeter fence for the site to close. They will then rummage through the bin bags for the information needed to commit ID fraud. Make sure those who commit this crime is brought to justice.
Finally, before I introduce the video below, take a moment to review the excellent articles published on the Nerd Wallet site, including their handy checklist.
The video below outlines some of the worst cases of cyber security and identity theft carried out to date. Watch this video, and make sure you are not the perpetrator's next victim!