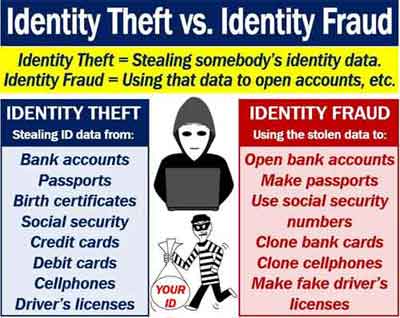
Common Types of Malware And How To Deal With The Risks Correctly
Different types of malware exist today, and it is likely you have heard about some of them. However, do you know exactly whey they are and what they do? More importantly, do you know how to deal with them if they cross your path?
Each type behaves in specific ways and have a different malicious intent. It is important you understand this to keep yourself safe whilst going about your everyday online life. A definition of malware can be given as:-
“All types of unwanted malicious software installed onto your computer device without your absolute consent.”
The aim of this section is to provide you with a basic understanding of all types of malware, so you do not underestimate its impact if you are affected or targeted.
We are all online and connected 24/7 these days. The proliferation of mobile devices, social media, and technologies such as artificial intelligence, presents too many opportunities for cyber criminals to easily exploit and take advantage of people in our connected world. This must change.
The second aim of this section is to arm you with the knowledge, tools, and techniques to protect yourself and your devices properly, just like a professional would.
Join The Human Byte — Get The Ultimate BIOS Update Guide
- Receive the Ultimate BIOS Update Pack
- Includes a set of checklists, flowcharts, and your Beep Code Finder support your BIOS update process
- Also includes a full set of eBooks including a Survival Guide and step-by-step Support Guide
- Receive regular emails with practical information you can use
- I only use your e-mail for the newsletter. Unsubscribe anytime.

Types of Malware | The Scourge of Ransomware on Society
Ransomware has grown to be one of the most popular types of malware that exists. It is a criminal industry worth billions of pounds or dollars, and has affected individuals, health services, and businesses across the world.
In its simplest form, ransomware is a software program that infiltrates your device, and blocks or encrypts valuable data files, so you cannot access them. The criminals then extort money from you before unlocking, or decrypting, your files, so you can access them again.
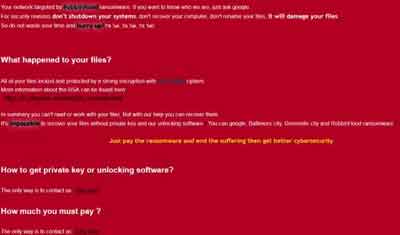 Types of Malware
Types of MalwareThe RobbinHood Ransomware Message That Appeared Across The City of Baltimore, USA
Source:- sophos.com
The RobbinHood ransomware attack in 2019 cost the city of Baltimore, USA, more than $18 million. The Wannacry attack of 2017 cost the NHS in the UK untold millions of pounds.
Ransomware infiltrates through social engineering e.g. realistic phishing e-mails that look legitimate, but contain masked links that trigger the installation of the malicious software in to your device, without you knowing about it.
Once installed, the ransomware program enables the cyber criminals to profile your activity, then target your key files that are most valuable to you for encryption.
From here the criminals employ several physiological techniques to extort money from you, including the threat of deleting your valuable files at an increasing rate, the longer you wait to pay their ransom.
Whatever you do, Do. Not. Pay. The. Ransom! You are unlikely to get your files back and even if you do, there is no guarantee your files will be readable. They are criminals, and they do not care once they have your money.
Make sure you have at least two good offline backups of all your important files. Regularly check the backups can be restored.
The sophistication of ransomware will continue to evolve. Fileless ransomware is emerging, where a software program does not necessarily need to be installed on your device. This type of attack infiltrates your computer's memory by exploiting flaws in legitimate applications or operating systems, and is much more difficult to prevent.
One option to reduce the risk of ransomware infiltrating your devices is to install a solution such as the Kaspersky Internet Security suite.
There are other products such as MalwareBytes that do the same job, and are even free of charge in some cases. I have MBAM installed on all of my device's ad it protects against many types of malware.
Spyware | A Veteran Malware Practice Since The 1990s
Spyware, and forms of Key logging and Adware, are software programs covertly installed on your machine that can capture your keystrokes as you use your device, and bombard you with various adverts based on your tracked online activity.
Spyware is an invasion of privacy. You are not aware of what the software is doing silently on your machine, and it is very likely you would object if you were given the choice to have the software installed or not.
Criminals can use this software to record your online banking details and other login details, for example. Adware can profile your online activity sufficiently over time to enable criminals to sell information about you to advertisers without your knowledge. Other forms of fraud and blackmail should not be ruled out either.
However, Spyware is often used to check the online activities by family members or loved ones. For example, to collect evidence against a cheating spouse, or to ensure their children's internet safety.
 Types of Malware
Types of MalwareKeylogging Spyware Example
Spyware has been around since the mid-1990s. Suppliers such as McAfee are very aware of these programs, and their Anti-Malware applications are excellent in identifying and removing such programs quickly and easily to minimize any damage.
However, this does not mean your device is safe. The fact Spyware could be installed on to your machine in the first place is a reg flag and a cause for concern. This is because the mechanisms or vulnerabilities exploited to access your machine in the first place are also used by much more sophisticated and damaging Malware.
If you have been subjected to Spyware, I would recommend you perform a full security review of your device, and take a good look at your web surfing habits. For example:-
- Make sure your operating system and applications have the latest security patches applied
- Remove any unnecessary software programs
- Make sure a good quality Anti-Malware suite is installed and up to date
- Regularly change your passwords and make them complex or passphrases
- Take regular backups of sensitive and critical data
The Software Application Security Patching Plan article focuses on keeping your devices protected against software vulnerabilities that could be exploited and put your personal data at risk.
For this article, I've taken the best practices businesses should follow, and adapted them for home users. Included is a six-step plan for home users that, I think, will serve you well for improving the security of your home devices.
The article also looks at the fundamentals of software patching, such as what it is, why it is important and how to automate software patching using native operating system settings, and 3rd party tools.
A modern form of security assurance that can protect your identity whilst online is to purchase a VPN, or Virtual Private Network, solution.
The Private VPN article was written by one of our guest writers, Chris Jones, from TurnOnVPN.
Technological advancements mean nearly every business is promoting the interconnection of numerous gadgets to deliver smart homes, smart vehicles, smart lights, smart TVs, smart locks, and other Internet-connected devices.
Consumers are getting tied up with all the benefits of the disruptive Internet of Things (IoT) without truly seeing how their own private data is being gathered and utilized.
This article focus on how VPNs protect your devices and you from the nasties that lurk online.
Types of Malware | Trojan Horses And The Damage They Can Cause
Trojan's are malicious software programs that are very well disguised as legitimate software applications.
They are an incredibly popular form of malware and are easy to create. In fact, millions of different Trojans are released every month. This is why they are so difficult to defend against.
Some of the most deadly Trojan's in history include Emotet, a sophisticated banking Trojan that cost the industry millions of dollars to resolve, and Zeus, another Trojan that targeted banks and multinational corporations.
Both were written to steal sensitive data including usernames and passwords, which is the key criteria for account hacking, which can be difficult to prevent once the cyber criminal has this information.
Account hacking is on the rise. There are at least 30 billion devices connected online, with each device having access to multiple accounts (mine mobile has over 40 different apps/accounts alone). That is lots of accounts for cyber criminals to have a go at.
Cyber criminals use various techniques to access your information, including phishing campaigns using fraudulent but realistic looking e-mails (see image below).
It is also reported that over 60% of people use the same password for all of their accounts. This is a convenience, both for you and the hackers!
In this article, we simply review good practices you can use to protect your online accounts.
Legitimate looking e-mails and attachments are just one of many ways Trojan's can infect machines. Phishing e-mail is also a well-known method for committing identity theft.
The Cybersecurity and Identity Theft article looks at ways to protect your identity online and how to report it if it happens to you.
In the UK, it is reported that the average household has up to 8 internet-connected devices, and 95% of Britons buy goods and services online.
With this level of connectivity and interaction online, we are more vulnerable to cyber criminal activity than ever before, and online ID theft is on the rise.
Do not be caught out by phishing e-mails. If they look too good to be true or ask for personal information, don to open.
If the questions, offers, or requests for information were being asked of you in 'real life', would your answers be the same as this chap in the hilarious video below?
Types of Malware | Hilarious Phishing E-Mails In Real Life Sketch Video
Identity theft is on the rise. It is imperative you understand how this can happen to you, and the damage subsequent fraudulent activities can cause. Have a look at the article above.
Another example of Trojan horses is legitimate looking antivirus programs.
Trojan's do not usually have the capability to replicate themselves on to other devices, on a network, like other types of malware can. However, they only need to get on to one networked device to start stealing sensitive information.
To protect yourself, you need a good quality anti-malware solution that is frequently updated with the latest information about new Trojan horses.
In the event you accidentally open that attachment, or runs that legitimate looking installation file, you want to be confident that your device security has your back.
Types of Malware | The Early Bird Catches The Worm
Worms are quite nasty. They are often initiated by dodgy e-mail attachments, similar to Trojan's. However, once they are on your machine or network, they can self replicate and infiltrate all other machines and accessible services.
Worms have been around for years, just like Spyware. They were the scourge of companies and IT support teams in the late `1990s are early 2000s, when e-mail was exploding in popularity.
All it takes is one person to open and click that dodgy link, or open that suspect attachment, and the entire organization would be affected. This typically looks like slower network performance, lost files, and full e-mail servers.
One of the most notorious worms this century is known as the ILOVEYOU worm.
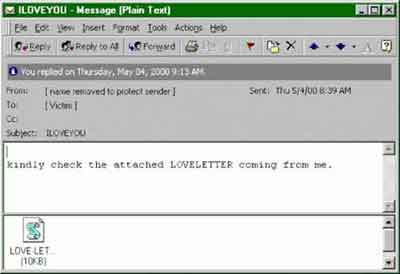 Types of Malware
Types of MalwareThe ILOVEYOU Worm That Caused Havoc Over 20 Years Ago
The ILOVEYOU worm originated in the Philippines and on the 5th May 2000, attacking millions of PCs worldwide. Once the attachment was opened, the script would overwrite random files, damaging our image files, music files and operating system.
The worm would then replicate by sending itself to all of your contacts in your address book.
Today sophisticated antivirus software and business systems, such as cloud-connected e-mail filtering systems, offer a level of protection against malicious worms.
However, it is essential we remain vigilant of e-mail attachments, even from those who we know and trust. How do you know whether they have been affected or not?
One of our guest writers produced an excellent article that is worth a read, on how to remain safe from computer threats.
The best computer protection article, written by Ken Wilson, a Security Specialist at ThePCDoctor, describes the various techniques to remain safe online, including education, firewalls, and backups.
Types of Malware | Do Not Risk Catching That Virus
A computer virus is what most people refer to when their machine is infected with a form of malware. The term is synonymous with most types of malware.
Computer viruses are small programs that get into your system and attach themselves in secret to your computer's operating system, applications, or data files. This is much the same way as a virus infects a human and multiplies.
Virus writers target vulnerabilities, for example, in an application's programme code, to enable their virus to do the damage they intend.
When you open your application or load your file, the virus is also loaded, and that triggers the damage.
The damage depends on the virus writer. Some cause little disruption such as an unwelcome message on your screen, Other cause significant damage such as deleting or amending key system files.
Traditional viruses that are written to cause damage are thankfully in the minority of malware floating around the Internet today. This is because there is no money to be made from it. They are also difficult to clean. Most antivirus programs simply quarantine the infected file, and it is up to you to replace it, or remove and re-install the affected software.
However, some modern forms of malware can be comprised of different malware types. For example, Stuxnet is a worm, a rootkit, and a virus.
Viruses spread like other forms of malware such as rogue e-mails, dodgy websites or illegal software.
The symptoms of a virus may vary, including:-
- Noticeably poor computer performance
- Your computer randomly freezes and reboots
- Peculiar system messages appear on your screen
- Applications loading on their own
- Files and folders randomly disappearing
- Disabled antivirus program
- Your antivirus provider's web pages refuse to load
It should go without saying by not that all your devices should have a good quality antivirus package installed from a reputable provider.
Antivirus packages scan computer files on request and in the background. Part of their analysis checks for any changes in file size and composition.
If the changes match the pattern of a known virus in the application's database, you are alerted.
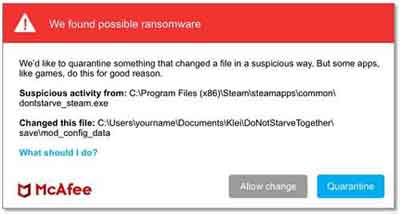 Types of Malware
Types of MalwareGenuine McAfee Computer Virus Protection Alert
Source:- mcafee.com
The key to dealing with malicious programs is to prevent them from entering your computer in the first place. Smart internet surfing habits and a good antivirus package are your starting points.
If your machine gets infected, the next best thing is to remove the offending virus quickly, if that is at all possible. At the least, deal with the issue as efficiently as you can.
Another of our guest writers produced an excellent computer protection article about how to protect yourself and your devices whist online.
The computer protection security article, written by Thomas Milva, an IT Security Analyst, focuses on cybersecurity and the fact that our online security is just as relevant as the security of our home or workspace.
You wouldn't allow any suspicious character to walk into your home and snoop around your possessions and people you care about, so why would you let that happen on the Internet?
The article looks at social media, considerations when downloading files, avoiding phishing scams and data backups.
Types of Malware | Rootkits And The Malware Explosion
Rootkits have been around for years as a means of launching cyberattacks. There is a thriving black market on the dark web for sophisticated and almost undetectable rootkits that can protect other forms of Malware from detection.
Rootkits are intuitive, so almost anyone could launch a malware attack if they so desired. This is how the cyber criminals make their money in the multi-billion dollar malware industry, and a reason why there is so much malware online today.
Their main use is to enable remote control access to your devices with full administrative rights. They inject themselves into the code of legitimate software of varying types, including applications, operating systems and even firmware.
This is what makes many rootkits almost impossible to detect and, therefore, remove successfully.
The W32/Rootkit.Avatar Source Code
Source:- welivesecurity.com
As with other forms of malware, rootkits infect your machine through phishing e-mails scams, nefarious websites and illegal software downloads. Fraudulent software masquerading as legitimate software are also a route on to your devices if you are not careful.
Some site visitors recommend Comodo Cleaning Essentials as an antivirus solution. However, my suggestion for using a more established anti-malware solution as a compliment to Comodo, which is excellent at identifying and removing rootkits, still stands.
Types of Malware | Botnet Attacks And The Legion of Followers
Bots are a type of software program that automates specific tasks on command. A botnet is simply a series of connected computers that are coordinated by the bot programme to perform instructed tasks.
Some botnets are designed for legitimate reasons. They can maintain large websites and manage large chat rooms, for example. However, they can be equally destructive when used for malicious reasons.
Once the bot is on your device, they usually communicate with a source or master server, then execute the plan alongside all the other devices that have been compromised.
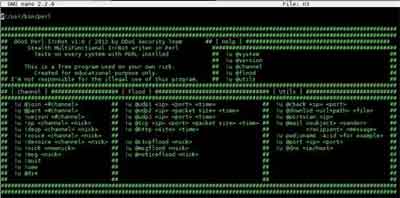 Types of Malware
Types of MalwareThe Shellbot Botnet Screen That Can Issue DDoS Attacks
Source:- securityaffairs.co
A common task executed by Botnets are Distributed Denial of Service attacks (DDoS). This is where the legion of botnet controlled devices send huge amounts of spurious data to a target, such as a website or organization's IT systems.
The volume of data botnets can send, overwhelms the system or website, and make it crash and unusable. This can result in a loss of business and revenue. It also presents an opportunity for the cyber criminals to hold the targets to ransom.
Botnets can also do things like generate fake internet traffic, inflate income for website owners, issue spam e-mail, and hold owner of botnet infected devices to ransom for the removal of the botnet software.
Bots and botnets are the surge on social media. Fake accounts in Twitter and Facebook, for example, entice people to interact and ultimately invoke malware that gains control of their device and then their personal information.
It is imperative we pay special attention to addressing our social media privacy. This article focuses on reducing the risk of information breaches on social media platforms.
We then focus specifically on the key Facebook and Twitter privacy settings that, I think, should be changed to protect your privacy. We then look at other methods to protect our online privacy.
Types of Malware | Dropping The Logic Bomb
Logic Bombs are malicious programs that are dormant once installed on a device, until the trigger event takes place. Just like its virus counterpart, the aims of logic bombs are to cause maximum damage.
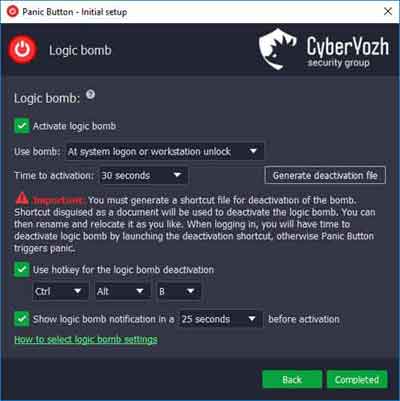 Types of Malware
Types of MalwareA Logic Bomb Setup Example
Source:- cyberyozh.userecho.com
As demonstrated by the image above, logic bombs can be set up to be dormant for months or even years, and then 'explode' as an unexpected event. This is one of the reasons why we need to be especially vigilant during holiday periods and other notable dates.
These events could include deleting an important file, or even destroying hard disks and other computer hardware components.
Logic bombs can also be written in the other forms of malware such as viruses, worms and Trojan horses.
As with all forms of Malware, it is beneficial to get into the habit of good internet behaviour, and avoiding bad practices.
Types of Malware | The Benefits of Multi-Factor Authentication
The benefits of multifactor authentication (MFA) cannot be underestimated. Traditional usernames and (or single factor authentication) are insufficient in today's world. Modern cracking techniques will work out what your password is in no time.
MFA is the modern approach to securing your access to online accounts and applications. The technique was developed based on three basic elements:-
- Something you know (Also known as Knowledge Factors)
- Some you have or own (Also known as Possession Factors)
- Something you are (Also known as Inherence Factors)
The benefits of multifactor authentication article introduce you to the MFA concepts, making it easier to understand, and therefore easier to set up and use.
We also look at how the MFA process typically works, and then review the rationale behind the benefits of multifactor authentication that we all experience.
Types of Malware | Artificial Intelligence and Machine Learning
Science fiction exaggerates the dystopian future where cyborgs from the future are ruling the world. The fact that the Artificial Intelligence we have only seen and read in science fiction is slowly becoming a reality, is something to behold.
Driverless cars, robots improving our health and services such as Siri, Alexa and chatbots, are just the tip of the iceberg of what's to come in the future.
However, appropriate cybersecurity measures need to be put in place, so the technology that is to improve our lives, doesn't wreck our lives.
 Types of Malware
Types of MalwareMachine Learning Examples
Source:- slideserve.com
In the Artificial Intelligence and Machine Learning article explores the topic in detail, investigating the benefits these techniques bring to improving our online safety, and the risk if they fall in to the wrong hands.
Windows Defender Firewall
The Windows Defender Firewall is a free security tool that come with Microsoft Windows, and it aims to protect your computer from all the nasties that exist on the Internet.
When you think about the different types of network traffic that enter and leaves your computer; Web Browsing, Applications, Games, E-Mail, etc., there is ample opportunity for malware techniques to infiltrate your devices, including phishing attempts, spoofing and ransomware.
Therefore, this article focuses on explaining what the Windows Defender Firewall is, and how it can be configured. We then look at how you can change the Firewall settings, and touch on the best practices for Firewall setup and protection, according to Microsoft. Firewall logging is also covered.
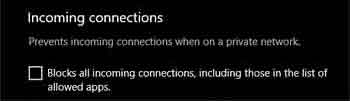 Malware Basics
Malware BasicsWindows Defender Firewall "Shield's Up" Blocking All Incoming Connections Option
Final Thoughts on The Types of Malware Covered
There are several types of malware that are written to undertake specific tasks, ranging from Spyware to Trojan Horses. Regardless of the types of malware that exist today, and in the future, you have a duty to yourself and your family to do all your call to protect yourself.
Also, don't forget to protect your mobile devices too. Apple devices and especially Android devices are also susceptible to malware. You just need to be careful when selecting the type of anti-malware package, so your mobile device does not slow down too much.
In this article, we have a look at what you can do to improve the security of your mobile phone, including creative PIN codes, network connectivity and application management. We also look at a list of other hints and tips you can take on board to protect your mobile.
 Types of Malware
Types of MalwareMobile Phone Security Awareness
Dot Lock Code Example
Source:- nerdstechnews.blogspot.com
ESET Mobile Security and Antivirus is a free solution that has excellent reviews.
This CSO article also describes different types of malware and how to recognize them. Exceptional read.
Finally, I would suggest you have a look at some malware articles in the site archive. Although the articles are not maintained, they are focused on the setup and configuration of some top antivirus provider products.
I find that although products evolve and improve, the fundamentals of how they should be set up and used do not change all that significantly.