HijackThis - Your Friend Against Problematic Malware
by Steve
(Manchester, UK)
HijackThis Scan Results
I use the HijackThis tool. I think it is a brilliant piece of freeware. It creates a snapshot of what is loaded on your computer.
The results of the snapshot are analysed to determine whether there is any specific types of Malware present.
In most cases, what is loaded on your computer is safe. However, some Spyware<, specifically those written to take over your browser and do things like change your home page or send your search results to another site, are so sneaky that even well known anti-malware tools such as Ad-Aware, will not detect or remove them.
I like HijackThis because it focuses on the MalWare writers' tricks they used to infect your computer.
You install the program, then click the Scan button for the scan to take place. It doesn't usually take too long.
If you have never used HijackThis before. I strongly recommend you DO NOT Analyse or Fix any of the items yourself. This is a tool for those who have a bit of experience with computers.
You don't want to remove files that could stop your computer from working properly!
I advise, instead of trying to work what the log file is telling you, upload it or copy it to a site such as HijackThis Log File Analysis Site.
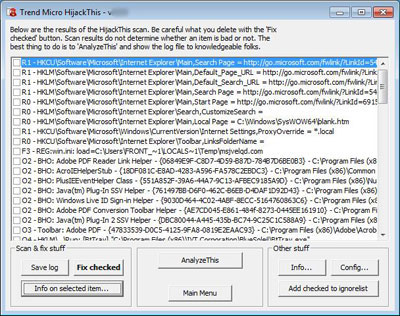
To achieve this, click the Save Log Button and save the log file to your computer. Open the saved file, copy the contents, then go to the above website and copy the details to the text box.
Click the Analyze Button. Scroll down the assessment and decide which entries need to be deleted.
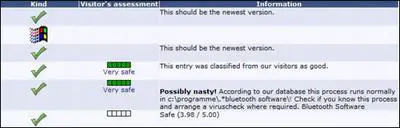
The visitor's Assessment and information columns are provided based on what others think of the entries.
For example, some are marked as Safe or Very Safe, and if you click these, a pop-up box appears with some more detail about what other visitors have said about that particular entry.
If the information says a log entry is possibly nasty, click the safety gauge, as it may be a legitimate file that you do not want to delete.
If you find something you decide to delete, search your log file within HijackThis to find the entry. Check the box, then click the Fix Checked Button.
Hopefully, you will find HijackThis helpful too.
Comments for HijackThis - Your Friend Against Problematic Malware
|
||
|
||