- Home
- Malware Basics
- Windows Defender Firewall
Windows Defender Firewall Setup And Troubleshooting
Stephen Harrison B.Sc. (Hons), M.Sc., MBCS, CITP
The Windows Defender Firewall is a free security tool that come with Microsoft Windows, and it aims to protect your computer from all the nasties that exist on the Internet.
Firewalls exist in both hardware and software format. Generally speaking, hardware-based Firewalls are used in corporate organizations, and form part of a wider cyber security setup; protecting up to thousands of computers, IT systems, and their sensitive data.
Software-based Firewalls tend to be found on personal computers, and are tasked with protecting your data and applications from the outside world, such as Public Wi-Fi services and the wider Internet.
When you think about the different types of network traffic that enters and leaves your computer; Web Browsing, Applications, Games, E-Mail, etc., there is ample opportunity for malware techniques to infiltrate your devices, including phishing attempts, spoofing and ransomware.
Therefore, this article focuses on the more complex of security tools, and likely the one that you are most unfamiliar with. We tend to leave the Firewall to its own devices, which is usually fine, but it's worth understanding this tool, so you can get the best out of it.
We start with a brief overview of the Windows Defender Firewall, then explore the configuration options. We then look at how you can change the Windows Defender Firewall settings, and review the best settings for your Firewall.
Keep up with the latest news and developments
Sign up to the eComputerZ Newsletter
The free A to Z of performing BIOS updates guide that anyone can follow.
✔ A checklist of important actions to perform throughout the update process.
✔ Further supporting information to aid your update plans.
✔ My unique approach for sourcing the latest BIOS versions for any motherboard manufacturer.
Sign up below for instant access to the guide, or by going to the Subscription page for more details.
I never share information with third parties and your details are secure.
I aim to issue newsletters at the start of each month.
Contents
The Windows Defender Firewall Overview
The Windows Defender Firewall is designed to protect your computer, applications and data from incoming, or inbound connections. This means by default, any data sent to your computer, that is from an application or service, that is not specified in the inbound rule list, will be blocked.
The benefit is that any spurious service on the Internet, that attempts to access your computer will be detected by your Firewall, and prevented from entering.
These attempts are usually hidden, and you would not know they were happening, unless you have alerts setup to advise you of access attempts. Often, these attempts are done using something called port scans. More on this later in the article.
Internet or network traffic that is allowed, or permitted, by your Firewall, is granted access to your computer, for example downloading a file from a good website.
The Windows Defender Firewall is also designed to protect outgoing, or outbound traffic. Just like external attempts to access your computer, there are also risks with your computer attempting to access services on the Internet.
For example, if you accidentally attempt to access a malevolent website, known to trigger ransomware attacks using certain ports, then you want your Firewall's outbound rules to block these attempts before a connection is established. This is done by your Firewall checking the traffic leaving your computer, against its outbound rules. If it's not on the list, it's not getting out!
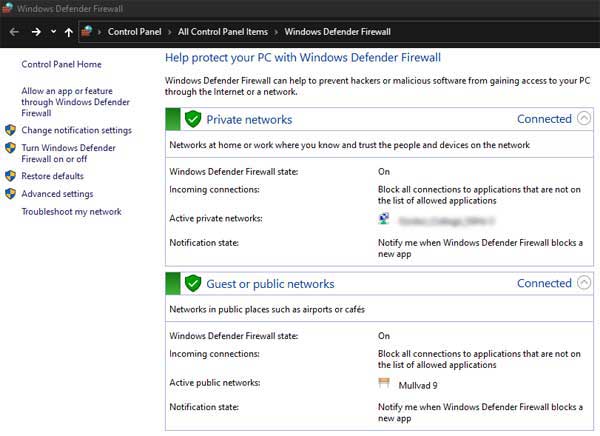
The Windows Defender Firewall typically looks like the image below when first opened. As you can see from my Laptop, the Firewall is switched on, it's blocking all incoming connections that are not specified in the inbound rules, and I have notifications set to inform me when the Firewall blocks a connection.
The Private Network is my connection to my home broadband service, and the Guest or Public Network is my VPN Connection (for added protection). Both are set up in the same way. There is a third connection type, or profile, but this is usually reserved for corporate organizations with "Domain Controllers".
 Windows Defender Firewall Overview
Windows Defender Firewall OverviewIn addition to inbound and outbound rules, the Windows Defender Firewall is also capable of Connection Security Rules. These are rules to enable, block or isolate connections to and from your computer.
For example, you may want to exclude another computer on your home network from accessing your device, or set up a secure connection between your computer, and another on your home network only. Generally, this feature is unused by home computer users.
There is also a monitoring feature which allows you to view your rules, for example, but not changes the settings.
In the next section, we look at Firewall rules in more detail.
Firewall Configuration Options
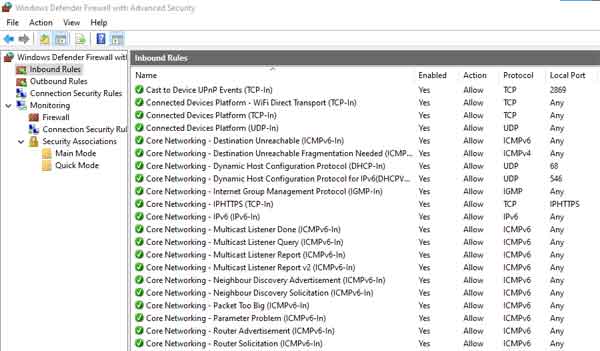
The Windows Defender Firewall Advanced Settings shows you all the Inbound and Outbound rules that are currently set up on your computer. There are over 500 rules set up on my Laptop alone, and over 18 parameters, or options, that can be configured.
Some configuration options are self-explanatory. For example, "Name", is the name of the Firewall rule, and should be descriptive to reflect the nature of the Firewall rule, as outlined in the image below.
 The Windows Defender Firewall Inbound Rules
The Windows Defender Firewall Inbound RulesOther configuration options are handy to know, such as any groups Firewall rules belong to. For example, the core Networking Firewall rules are all grouped together, in a group called Core Networking. You can filter on this group name to see all the associated rules.
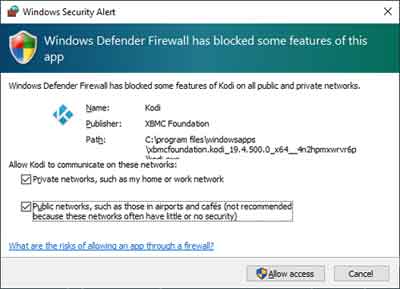
However, the configuration options I prioritize include the Enabled status, which shows whether a specific Firewall rule is enabled or not. This is handy for troubleshooting. For example, if an application is not connecting properly to an external source, and/or accepting incoming connections from external sources, then a warning message appears on-screen.
 Windows Defender Firewall
Windows Defender FirewallApplication Blocking Message
I also focus on the Action status, which shows the Firewall rule to be Allowed or Blocked. Firewall rules and configured with a specific set of criteria, or conditions, which are then Allowed to take place, or are blocked from taking place.
Protocols and Local Ports, alongside IP Addresses, are key in Firewall rule criteria. Protocols are a set of conditions for the transmission of network (Internet) data. There are several protocols in existence, but for the Windows Defender Firewall, the two protocols in use are TCP and UDP.
TCP stands for Transmission Control Protocol, and is used by applications and services that require a more reliable and controlled approach to how they transmit and receive data, and is not necessarily dependent on the speed at which the data is sent/received. For example, the sending and receiving of e-mails, and data files, uses TCP.
UDP stands for User Datagram Protocol, and is used by applications and services that a more dependent on speed, and less dependent on reliability or the order in which the data is transmitted and received. For example, streaming media, such as Netflix, and Internet Telephone calls, use UDP.
Some applications and services use a combination of both TCP and UDP protocols.
Ports are essentially used for the transmission of data relating to a specific service. For example, secure Internet data transmissions are undertaken over port 443 (https). Unsecured or traditional Internet traffic is transmitted over port 80 (http).
In the context of Firewall rule criteria, the protocol and the port are critical. For example, you may create a Firewall rule that blocks an application from transmitting data over TCP/Port 80, and only allows the transmission of data over port 443.
In the next section, we look at how to manipulate Firewall settings, and how to create Firewall Rules. We also look briefly at Firewall Logs.
How To Implement Firewall Configuration Settings
Windows Defender Firewall rules can be enabled or disabled. A disabled rule will not run, and the criteria for a given application or service will be ignored.
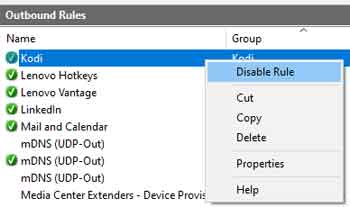
As is usual with Microsoft products, there are several ways to undertake an action. The quickest way, in this instance, is to right-click the Firewall rule in question, and select "Disable Rule" from the drop-down menu.
 Windows Defender Firewall
Windows Defender FirewallDisabling Outbound Rules
It is worth noting that you should disable a Firewall rule, rather than delete. It will do no harm in a disabled state, and you never know when you might need it again, for example, if applications and services start behaving strangely.
To Allow or Block a Firewall connection, open the rule in question, and select the "Allow the connection" or "Block the connection" option. As outlined in the image below, a blocked connection changes the icon next to the rule name.
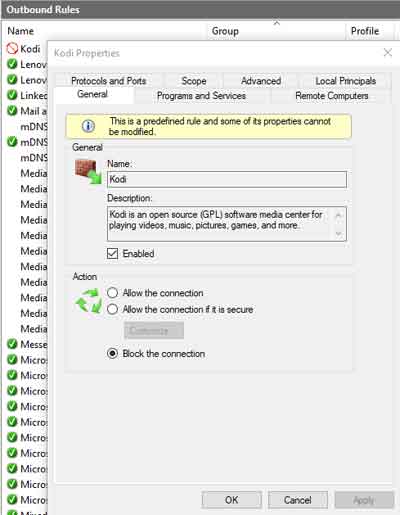 Windows Defender Firewall
Windows Defender FirewallBlock The Connection
Creating a new Firewall rule is simple, but also very effective. The rule will do what you tell it to do, so be sure you know what you are doing first!
By way of example, I created a new temporary outbound Firewall rule, that disabled all Internet traffic from my Laptop. I right-clicked the Outbound rules section and selected the New rule... option. I then selected Port > TCP > All Remote Ports. The Internet uses may different ports, so instead of specifying many port numbers, simply select all. From here, I specified to Block the connection, on all profiles (Private/Public), and then named my rule.
From the Images below, I found that when I loaded Microsoft Edge, and attempted to access my website, I was unable to. The web browser knows the Internet is blocked on my computer, and even suggests checking the Firewall configuration as per of a troubleshooting approach.
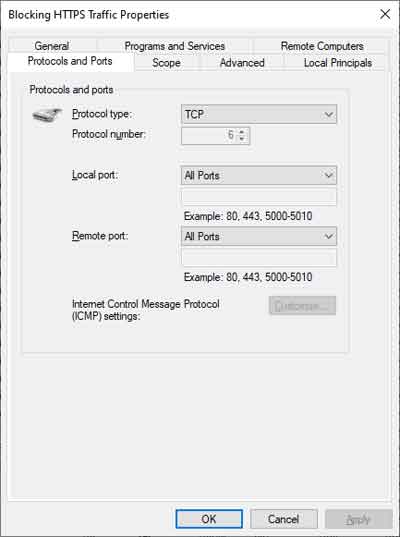 Windows Defender Firewall
Windows Defender FirewallCreating An Outbound Firewall Rule
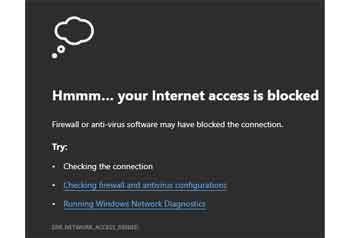 Windows Defender Firewall
Windows Defender FirewallImpact of Disabling Internet Traffic
Log files are the bible for IT professionals. They are one of the first go to sources when troubleshooting issues, so long as what is being logged is related to your issue.
The Windows Defender Firewall has log capability for both dropped packets, i.e. when connectivity is intermittent or disrupted, and successful connections, i.e. when you are testing specific connectivity.
Log files can be difficult or cumbersome to interpret. The image below is the result of activity following the Internet Traffic Blocking rule.
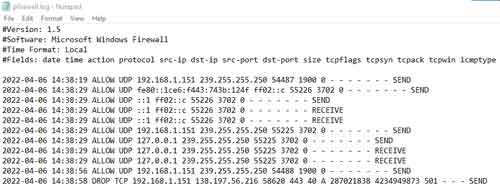 Windows Defender Firewall
Windows Defender FirewallLog Report Example
I suspect in most cases, home computer users will not need to create or amend any of their Firewall rules, but it is useful to know and understand how Firewalls work, especially in the context of troubleshooting.
I also think Firewall logging is difficult for most home computer users to interpret, so again, for awareness.
In the next section, we look at some of the best practice Firewall configuration settings and features.
Best Practice Firewall Configurations and Features
Microsoft recommends you do not change any of the Windows Defender Firewall default settings. They are set is a specific way to protect computers in most scenarios. This also goes for the Firewall rules.
In addition, Microsoft recommends that if you do create new Firewall rules, that you make them as specific as possible. This is common sense. Firewalls are a security tool, and therefore, if you are creating "holes" in your Firewall for any given reason, then the rules should be set up for what you need only, no more, no less.
It is also worth knowing about the "Shield's Up" feature, which can prevent immediate and long-term damage from an active external attack on your device.
Shield's Up is initiated by blocking all incoming connections, and you can do this for each profile, by searching for Firewall & Network Protection in Windows Settings.
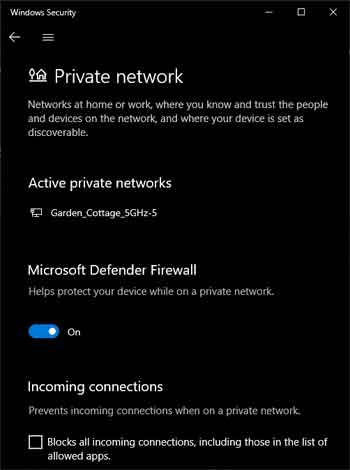 Windows Defender Firewall
Windows Defender FirewallBlock All Incoming Connections
It is worth mentioning that if you find yourself in a muddle, reset your Firewall back to the default settings. At the very least, this will put your device back into working order.
Windows Defender Firewall Final Thoughts
Firewalls, and Firewall configuration, are huge topics. We have looked at what Firewalls are, the main features of the Windows Defender Firewall, configurations settings and considerations, implementing new firewall settings, and home computer user Firewall best practices.
The Windows Defender firewall should be part of a wider security setup on your computer, which is not too dissimilar to corporate organizations, i.e. ensure you have competent Anti Virus and Malware applications installed, and that they are constantly updated, with regular scans of your devices. I would also recommend a good VPN Service.
I'll leave you with some good quality links to other articles that supplement this page. The How-To-Geek article on using the Windows Firewall With Advanced Settings is an excellent source for information such as what each of the Firewall Rule parameters are, and their article on Firewall Application Blocking is explained well.
Finally, the PDQ article on setting up the Windows Defender Firewall Log is useful if you want to explore the world of computer logging and log files.
- Home
- Malware Basics
- Windows Defender Firewall
