- Home
- The 2010s
2010s Computer History
"I'm Just Another Guy" - Ed Snowden, June 9th 2013
Stephen Harrison B.Sc. (Hons), M.Sc., MBCS, CITP
2010s computer history is packed with rapid technological advancement, and of course, some controversy. The last decade has seen radical changes in the way we interact with computing technology.
Remember the Raspberry Pi Computer This little device, which was six years in development, was released at its lowest cost of just £22, for the first time in February 2012.
Based on the LINUX operating system, the UK Government and supporters wanted the machine to help improve the level of programming skills among UK children.
This is just one example of major computing events that has occurred throughout this decade. The aim of this section is to delve deeper into some of these momentous events.
 2010s Computer History
2010s Computer HistoryThe Raspberry Pi (2012)
Source:- phys.org
Keep up with the latest news and developments
Sign up to the eComputerZ Newsletter
The free A to Z of performing BIOS updates guide that anyone can follow.
✔ A checklist of important actions to perform throughout the update process.
✔ Further supporting information to aid your update plans.
✔ My unique approach for sourcing the latest BIOS versions for any motherboard manufacturer.
Sign up below for instant access to the guide, or by going to the Subscription page for more details.
I never share information with third parties and your details are secure.
I aim to issue newsletters at the start of each month.
Contents
2010s Computer History Milestone | The Apple iPad
The Apple iPad mobile device is still one of the most popular tablets in the world. Even the Business market is buying in to Apple mobile technology.
In the technology world, these landmark advancements do not appear out of nowhere. They tend to evolve, through trial and error, with lots of mishaps along the way.
The Apple iPad Revolution article describes rise to fame of this device, starting in 2010 with the release of the first generation iPad.
 2010s Computer History
2010s Computer HistoryThree Generations of the Apple iPad
Source:- CNet.com
The article also covers some IT Industry early efforts at mobile computing, including Tablet PCs and the Personal Digital Assistants (PDA's). In fact, the notion of mobile computing goes back over 40 years to 1968!
Return to the Table of Contents
Hardware and Software Vulnerabilities
The sophisticated exploitation of software vulnerabilities defines the underbelly of 2010s computer history. Despite all the good advances we have seen such as Artificial Intelligence, Robotics and Wearable technologies for improving healthcare, criminality became very much an online event.
In 2018, the world was made aware of two new and serious vulnerabilities, called Meltdown and Spectre. These were specifically hardware-related vulnerabilities in the majority of Intel Processors since 1995. Think of the millions of devices affected!
Meltdown would basically allow malware to read the data of running software programs and the operating system in the system memory, or RAM. From here, passwords and sensitive data could be copied, or locked, and held to ransom. Multi-Factor Authentication is a must if available to help protect online accounts.
Spectre would basically allow malware to trick computer applications into leaking their data. This is because the secure isolation between running applications is flawed.
 2010s Computer History
2010s Computer HistoryMeltdown (Shield) and Spectre (Ghost) Logos
Source:- malwarebytes.com/
The majority of world software providers issued security patches for Meltdown and Spectre.
However, with the vulnerabilities present in critical business infrastructure, organizing the downtime to apply security patches is often a difficult task.
In my 20+ years of experience, convincing decision makers that taking a critical system offline, without any noticeable benefit to the business when services are resumed, is a difficult task.
I expect the 2020s not to be any different, despite the warning and events of the 2010s.
Return to the Table of Contents
Cyber Attacks
We cannot discuss this era without mentioning cyberattacks. The decade is remembered for events such as the Stuxnet virus attack and Wannacry ransomware attack.
Stuxnet was first discovered in early 2010 and was responsible for causing considerable damage to Iran's nuclear programme.
The worm or malicious code targeted Supervisory Control and Data Acquisition System (SCADA) and Programmable Logic Controllers (PLC) used in industries such as the nuclear industry to control machinery and the deployment of gasses.
Stuxnet is a malicious computer worm that replicates itself on to other computers once it has infiltrated a computer network. Once it could influence the SCADA and PLC devices, Iran's enriched uranium was effectively destroyed, putting their nuclear programme back years.
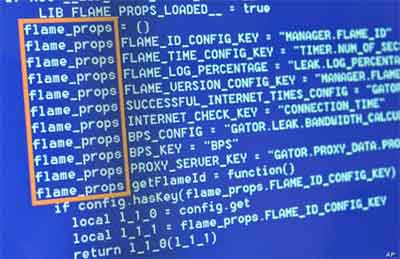 2010s Computer History
2010s Computer HistoryPart of The Flame Toolkit Code Used to Launch The Stuxnet Worm
Source:- voanews.com/
Zero-day attack worms like Stuxnet are difficult to stop. Generally, all computers in an organization need to be shut down immediately to prevent further spread. This is where the damage is done.
From here, the vulnerability in the software that the worm is exploiting needs to be patched, coupled with an update from anti-virus companies to detect and nullify further threats from the worm in the future.
It is understood Stuxnet was developed by the United States and Israel, using a sophisticated espionage toolkit called Flame, and was targeted specifically an Iran's nuclear industry.
These types of attacks in the 2010s became known as cyber warfare, and the malicious code itself known as a cyber weapon.
It is expected this type of warfare will continue in to the 2020s and beyond, and will no doubt become more sophisticated as time goes on.
Seven years later, the world was subject to another major cyberattack. In May 2017, the Wannacry ransomware attack devastated the National Health Service (NHS) in the UK, and other major organizations around the world.
Another zero-day even, Wannacry was developed as ransomware to extort money in the form of Bitcoin by the cyber criminals behind the attack.
The developers exploited software vulnerabilities in Microsoft's Operating Systems, named Eternalblue and DoublePulsar. These vulnerabilities are alleged to have been stockpiled by the NSA. However, because cyber criminals acquired knowledge about the vulnerabilities, the NSA informed Microsoft, who issued a patch before the Wannacry event.
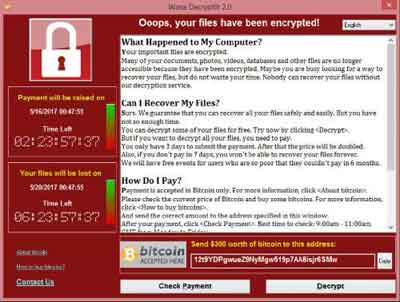 2010s Computer History
2010s Computer HistoryThe Wannacry Ransomware Attack Message Displayed on Infected Devices
Many organizations are not efficient at applying security patches, and therefore ransomware such as Wannacry can easily exploit these flaws to the financial gain of the cyber criminals.
This is another example of what, I think, is to come throughout the next decade and beyond.
Return to the Table of Contents
Edward Snowden
Ed Snowden is the notorious U.S. whistleblower who worked for the Central Intelligence Agency (CIA) and leaked highly classified information from the National Security Agency (NSA) in June 2013.
The data included detailed knowledge about global surveillance programs, including covert access into private citizen e-mail and instant messaging accounts by U.S. authorities, and citizen mobile phone location data, to name but a few.
The U.S. authorities were quick to issue a warrant for Snowden's arrest, but he eventually fled to Russia. From a government perspective, what Snowden did put many undercover agents lives at risk.
From Snowden's perspective, he sees what he did as his civic duty, as citizen's should have a right to know when their governments and people in power are up to, and how their private data, is actually not private.
Where do you sit in the Edward Snowden Leaks debate?
 2010s Computer History
2010s Computer HistoryEd Snowden - The CIA Whistleblower
Source:- wikipedia.org
From Facebook and Cambridge Analytica's alleged manipulation of data to influence elections and referendums in the late 2010s, to the 11.5 m leaked Panama papers from the offshore law firm Mossack Fonseca that outed rich individuals tax avoidance schemes, whistleblowing in a connected digital world is likely set to continue in the coming decades.
Return to the Table of Contents
Silk Road
The Silk Road was an online black market site only accessible on the Dark Web through a TOR, or The Onion Ring, Web Browser.
The Dark Web has no jurisdiction and this enabled the founder, Ross Ulbricht, to set up the site in February 2011.
The site mainly sold illegal drugs, which accounted for 70% of the total trade. Other illegal products included fake drivers licences. Over an estimated 2 years period, Silk Road made over 1.2 m transactions and collected over 9.5 m bitcoins, or $1.2bn in revenue.
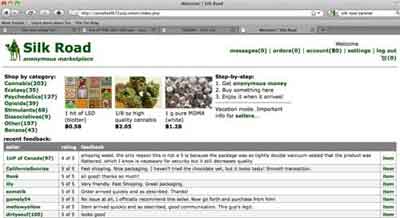 2010s Computer History
2010s Computer HistoryA Screenshot of Silk Road on the Dark Web
Source:- medium.com
In October 2013, the Federal Bureau of Investigation (FBI) seized and shut down the site. Its founder was arrested and ultimately sentenced to life in prison without parole for his crimes on the 29th May 2015.
 2010s Computer History
2010s Computer HistoryThe Message Greeting Silk Road Visitors After It Was Seized By The FBI
Source:- wikipedia.org
Silk Road is just one of many sites on the Dark Web, including Black Market Reload, which sold illegal drugs and other illegal merchandise such as stolen credit cards and firearms.
It will come as no surprise after Silk Road collapsed, the owner of Black Market /reload shut down their site.
The Dark Web is likely to remain constant as a hotbed of illegal activity in to the next decade, and potentially beyond. This is despite the increase in law enforcement combing the Dark Web and targeting the shutdown of illegal activity.
Return to the Table of Contents
DeepMind Artificial Intelligence
Founded in September 2010, DeepMind Technologies develops Artificial Intelligence (AI) systems to "solve problems and advance scientific discover for all".
AI is basically an artificial neural network that aims to mimic human short-term memory. Based on machine learning, early successes included the AlphaGo program that beat a European Go Champion in October 2015.
Following DeepMind's gaming successes, it turned its attention to more serious issues, such as solving the problem of protein folding in 2016.
This is an incredibly difficult problem to solve in science, but the evidence suggests DeepMind is making good progress understanding this issue as the 2010s came to an end.
 2010s Computer History
2010s Computer HistoryDeepMind Logo
Source:- venturebeat.com
The quality AI can bring to people's health and well being, such as supporting clinicians in diagnosing Radiology scans, there are still issues that need to be addressed, including data security, and ultimate control over AI automation.
Return to the Table of Contents
Windows 10
Microsoft Windows 10 was made available to the public on the 29th July 2015. It superseded the ill fated Windows 8, released in 2013.
Windows 10 succeeded where Windows 8 failed in delivering a consistent user experience across different devices classes, i.e. desktop PC, Laptops and Tablets.
The Operating System's security was also improved, including improvements to biometric authentication through the Windows Hello platform. Microsoft Edge was also introduced as the successor to Internet Explorer.
Other features in the new operating system includes Cortana, Microsoft's equivalent to Apple's Siri, and improved parental controls.
In a change to previous operating systems, Microsoft release feature updates every six months.
Microsoft tends to release a new operating system every 10 years. Windows 10 mainstream support ending on the 9th January 2024.
 2010s Computer History
2010s Computer HistoryMicrosoft Windows 10 Graphical User Interface (GUI)
Return to the Table of Contents
Spectre and Meltdown
Spectre and Meltdown are a collection of critical vulnerabilities found at the hardware level of almost all Central Processing Units. They were officially made public in January 2018, by cyber security researchers in Google's project zero team.
The Spectre and Meltdown vulnerabilities present an opportunity for cyber criminals to execute carefully crafted malware, and effectively have access to critical and sensitive information on your device that is running at that time.
Almost all computers worldwide were affected, and the efforts in to fixing these vulnerabilities was difficult, considering any fixes can technically slow down device performance.
The Spectre and Meltdown article looks at each vulnerability in more detail; what they are, and how they "work". We then look at the consequences of these vulnerabilities in more detail, and cover the more common questions asked about each vulnerability type.
Return to the Table of Contents
Google DeepMind AI
The Google DeepMind AI initiative is one of the breakthrough moments in the 2010s. Artificial Intelligence is evolving until now, but its origins go back to the 2010s.
In this article, we look at the history of DeepMind AI; what it is and how it originated, and its acquisition by Google in 2015.
We then look at the main pros and cons of Artificial Intelligence, which is a source of strong debate in my experience. We then look at specific technologies that AI, and DeepMind AI, have evolved in the subsequent years, including Chat Bots and Healthcare (a subject close to my heart).
Return to the Table of Contents
2010s Computer History | Final Thoughts
2010s computer history is packed with an eclectic mix of impressive technological advancements, coupled with some serious issues that impacted human society throughout the decade.
Google Glass, Streaming TV, Wireless Air Pods, Virtual Reality Headsets, Internet of Things, Big Data, Cryptocurrencies, the list of new technologies is endless.
The video below is a review of the best new technology released in the 2010s.
A Review Of The Best Technology Released In the 2010s Video
Having lived though the 2010s in a technical leadership position, I can honestly say the changes I have witnessed have, overall, been for the betterment of human society. I am looking forward to what the next decade brings.
For more information on computing events, take a look at Computer Hope's history section.
What a decade for technology!
- Home
- The 2010s

