- Home
- Articles | Security
Old Computer Software Programs | Cyber Security
Stephen Harrison B.Sc. (Hons), M.Sc., MBCS, CITP
Old computer software programs are very popular for numerous reasons, including familiarity, cost (cheap or free) and compatibility with older hardware. Often, newer software requires more powerful hardware to run and perform efficiently.
Here, we focus on written articles that have been archived on eComputerZ, covering cyber security tools and services.
This includes anti virus software such as McAfee and AVG, anti malware programs such as Malware Bytes, and stealth removal tools such as Stinger.
To compliment the archived articles I've added a section exploring why Cyber Security is essential when using older software programs.
Keep up with the latest news and developments
Sign up to the eComputerZ Newsletter
The free A to Z of performing BIOS updates guide that anyone can follow.
✔ A checklist of important actions to perform throughout the update process.
✔ Further supporting information to aid your update plans.
✔ My unique approach for sourcing the latest BIOS versions for any motherboard manufacturer.
Sign up below for instant access to the guide, or by going to the Subscription page for more details.
I never share information with third parties and your details are secure.
I aim to issue newsletters at the start of each month.
Contents
Why Do We Need Cyber Security When Using Old Software?
The popularity of old computer software programs is underlined by the fact that there are so many websites where you can download the applications of yesteryear.
Whilst I understand and appreciate the reasons why old software continues to be used by millions of people, there are cyber security risks that need to be reduced or even mitigated, where possible, if you are to continue using outdated applications.
All software vendor business models are roughly the same. They develop and release a new application or operating system, and provide support including security and functionality patches, for a limited period of time. This could be 1 year, 5 years or even 10 years.
Then the software vendor releases a new and different application or operating system, which could also be an evolution of the software that is due to be discontinued.
Support for the older software is reduced. Security patches are not as detailed or frequent, and functionality improvements cease. From here, support is restricted (and more costly in some cases), to the point where you have had sufficient time to invest in the new product.
Ultimately, the software officially reaches its published end of life, when no further support or security patches are released. Any vulnerabilities remain, and as more are discovered by cyber criminals, the more change there is of exploitation.
Imagine if this was your car, and the manufacturer said after a certain date you could no longer buy spare parts or get it serviced. This is the frustrating aspect of the software market ad its cradle to grave ethos.
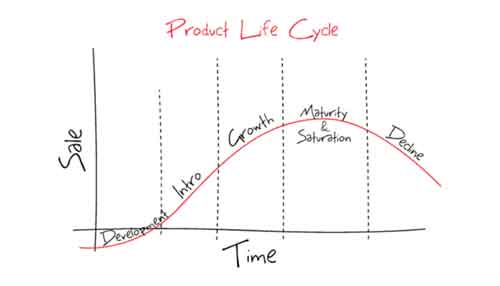 Old Computer Software Programs
Old Computer Software ProgramsSoftware Lifecycle Stages
Source:- medium.com
The exploitation of old software is increasingly easy for cyber criminals. There are no time constraints or risk from their perspective of the software being patched. They can therefore bide their time and plan their attacks meticulously.
Ransomware attacks, identity theft and data theft are a real risk, especially if your device is online, which applies to the majority of us.
In addition to the cyber security risks, there is an added concern of keeping your software working when you replace your device, so it can continue to be used. Take a look at the old software article for some pointers on how you can do this using virtual software.
My view is to keep unsupported software on a virtual machine (VM). The VM can be 'air gapped' from the Internet and other resources on your machine, and restricted in terms of service access e.g. USB sticks that could introduce malware. Alternatively, take a look at the Sandbox option.
With that in mind, the next section runs through legacy cyber security software articles written in the early days of eComputerZ. It is worth noting that the majority of these products are still available today (in supported versions, of course).
Return to the Table of Contents
Site Archive | Cyber Security
Most home users know about viruses, and have a computer virus removal program installed for protection.
However, this is just one type of malware. Other types of malware have exotic names like Trojan Horses, Worms and Adware. Each type has different malicious intent and should be avoided at all costs.
When you think about the explosion of social media in particular, you are creating more personal data now than ever before. Cyber Criminals can steal and sell your identity on the dark web, or hold you to ransom. Malware written to cause disruption to your machine is generally on the decline.
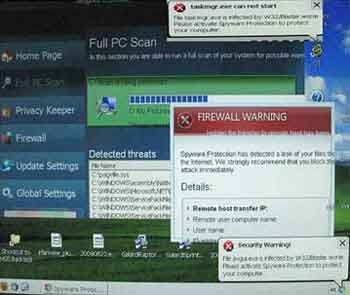 Old Computer Software Programs
Old Computer Software ProgramsFake But Realistic Looking Anti-Malware Program
Anti Virus applications scan computer files on request and in the background. They search for any changes in file size and composition.
If the changes match the pattern of a known virus in the application's database, you are alerted. The computer virus removal process can then begin.
Modern programs also monitor for other common malware such as Trojans and worms, and more.
Part 1 Free Virus Removal Software is the first of a 2-part series looking at popular free anti virus programs such as the AVG Virus Software.
We also look at how to perform an industry trade secret to test that your computer virus removal program is performing as expected.
Part 2 Free Computer Virus Scan looks at some tools that are freely available from anti virus companies.
Free utilities such as the ones we look at are essential support for protecting your home PC. Your anti virus program may find some viruses difficult to remove.
Learn how to download and use these stealth tools. Chances are you will need to use them one day.
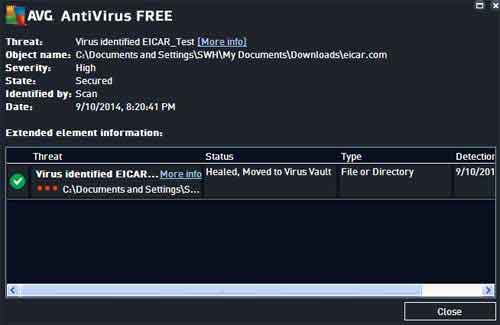 Old Computer Software Programs
Old Computer Software ProgramsAVG Detecting A Virus
Anti Malware software looks at the different types of software written to remove nasty programs and protect your PC. There are commercial programs, free software and websites that remove malware online.
There are also rogue malware programs that damage your machine as mentioned above. You can avoid these nasty programs with a few simple techniques.
There are also websites that suggest they remove nasty programs from your PCs. These sites cannot be trusted! It is most likely a scam.
Malware Bytes is arguably one of the best Malware removal programs available. Part 1 of the tutorial series Malwarebytes Download looks at how to download and install the program.
Part 2 Malwarebytes Anti Malware looks at how to use the program to the best of your advantage.
 Old Computer Software Programs
Old Computer Software ProgramsMalwarebytes in Action
Microsoft developed the Microsoft Malware Removal Tool to help prevent nasty programs attacking their Operating Systems.
This is a free stealth removal tool. This section looks at how to obtain and apply the malicious software removal tool, which is updated by Microsoft on a monthly basis.
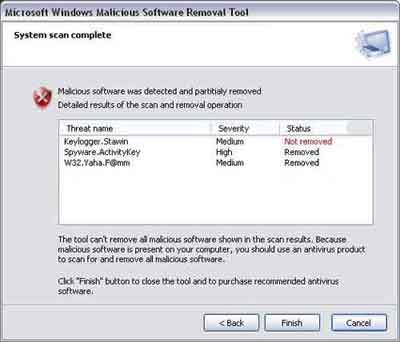 Old Computer Software Programs
Old Computer Software ProgramsMicrosoft Anti-Malware Removal Tool
McAfee is one of the largest security companies in the world. It is owned by the Intel Corporation, famous for making computer processors. A 4-part series dedicated to McAfee software was written to help users with their McAfee options.
 Old Computer Software Programs
Old Computer Software ProgramsMcAfee Free Virus Scan Package
The McAfee Free Virus Scan section talks you through installing the trial version of the McAfee Antivirus program, and how it protects your machine.
Commercial Organizations such as McAfee also have many free utilities on their website that can help you further protect your devices. Are you aware of them?
Visit the McAfee Computer Virus Remover section where we look at stealth tools such as Stinger and GetSusp.
Do you want to uninstall McAfee antivirus? There are circumstances where you might want to do this, e.g. you decide to use another antivirus package.
Removing McAfee products appears to cause many home users problems. For various reasons, the programs have not removed cleanly, causing your computer to become unstable.
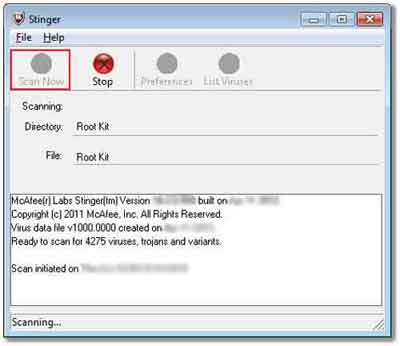 Old Computer Software Programs
Old Computer Software ProgramsStinger In Action
The McAfee Removal Tool section walks you through the process professional computer technicians follow when uninstalling an application goes wrong.
Once you know the secret, you can avoid issues that blight other home computer users! However, please ensure you have a suitable computer virus removal application available to install!
The McAfee Customer Service section looks at what McAfee offers its customers that you can take advantage of.
This includes free utilities such as the virtual technician and the security scan plus tools. Customer service advice on how to surf the Internet safely and how to contact McAfee directly is also provided here.
A very popular virus removal tool at the time was Microsoft Security Essentials, In a 3-part tutorial we looked at how to download, install and use this program to get the most out of it.
Microsoft Security Essentials reached end of life on the 14th January 2020 and is no longer available for download. Microsoft will continue to release signature updates (including engine) to service systems running MSE until 2023.
Part 1 looks at the download and install steps, and also looks at what you should do before you install MSE.
Part 2 looks at real-time protection, proactive scanning options and what to do if a malicious program is detected on your computer.
Part 3 looks at how to configure MSE. There are several options to consider for the application to suit your personal circumstances.
Malware causes many problems for home users like us. However, we can minimize the risk of infection by following the good practices of a typical computer support professional.
The main thing is not to worry too much. Malicious software is avoidable most of the time, and if you do contract an infection, there are many tools available to help you remove it cleanly.
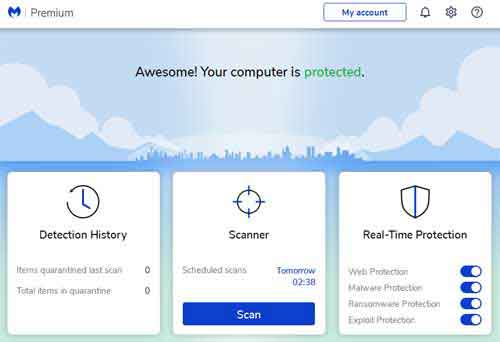
One of these tools is Norton Anti Virus Protection. This is a product that is much improved upon earlier iterations.
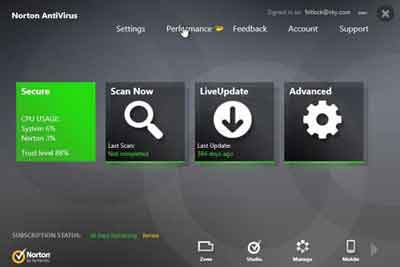 Old Computer Software Programs
Old Computer Software ProgramsNorton Anti Virus Protection Dashboard
With reduced CPU and RAM utilization when performing scans, and with integrated mobile and social media scanning, it is argued Norton is once again a credible player in the commercial anti virus market.
Return to the Table of Contents
Old Computer Software Programs | Final Thoughts
Old computer software programs appear to be here to stay, so we may as well embrace them and set up our working environments for maximum protection against cyber criminal activity. I hope the archived articles in this section have proven useful for you today.
To underline the importance of cyber security take a look at this well-written article discussing the security risk of outdated software.
Finally, if you are still intending on using old software, take a look at the vintage software collection site.
- Home
- Articles | Security
