Mobile Phone Security Awareness For Everyday Smartphone Users
We all need a degree of mobile phone security awareness if we are to protect our equipment in a rapidly evolving cybersecurity crisis.
Modern Smartphones are essentially (expensive) portable microcomputers that contain our lives, from traditional phone information such as contacts and telephone numbers, to accessing our social media platforms, banking systems, personal information such as photos and videos, and our e-mail accounts, to name but a few.
We are all one click away from infecting our devices with malware that could ruin our lives. Smartphones are being increasingly targeted with malware through methods such as legitimately looking, but infected apps, and when we consider the fact that Smartphones, and even tablet computers, are generally less secure than traditional computers, this underlines the need to improve our mobile phone security awareness.
In this article, we have a look at what you can do to improve the security of your mobile phone, including creative PIN codes, network connectivity and application management. We also look at a list of other hints and tips you can take on board to protect your mobile.
Join The Human Byte — Get The Ultimate BIOS Update Guide
- Receive the Ultimate BIOS Update Pack
- Includes a set of checklists, flowcharts, and your Beep Code Finder support your BIOS update process
- Also includes a full set of eBooks including a Survival Guide and step-by-step Support Guide
- Receive regular emails with practical information you can use
- I only use your e-mail for the newsletter. Unsubscribe anytime.

PIN Codes
One of the first steps you should take is to put a good PIN code or Key lock code on to your device. Reports suggest over 50% of Smartphones do not have a form of password security for authorized access (when switched on or woken from standby).
Traditional PINs are where you enter a 4-6 digit code each time you want to access your mobile phone. Often a biometric authentication can be added, such as a fingerprint or retinal scan.
Whilst this is OK, there are techniques that can interpret what your PIN code is, which means a PIN in itself, even when changed regularly, is not the most secure method of locking your Smartphone available.
Android devices incorporate a pattern lock, or dot lock facility, which is a more efficient method than entering passwords or PIN's, and due to random patterns, improves device security.
Pattern lock is a form of shape or pattern that is drawn on the screen of your mobile phone to enable, or authenticate, your access.
Pattern lock is essentially a long PIN code, but is drawn on the screen in a 'random' pattern style, as shown in the example below.
 Mobile Phone Security Awareness
Mobile Phone Security AwarenessDot Lock Code Example
Source:- nerdstechnews.blogspot.com
The video below gives you some ideas of what patterns to introduce. Some are more difficult to interpret than others. It may take some practice, but once mastered, your device will become very secure to access.
Top 5 Pattern Locks Video
However, a very secure device to access doesn't mean impossible to access. What is to stop a criminal from removing your mobile's SIM card and inserting into another device?
The answer, where possible, is to put a PIN code lock on to the SIM card. This is where you need to enter the code before the phone can boot and subsequently connect to a mobile network. It is similar to a BIOS password.
In the next section, we delve into security measures you can put in place when connecting your Smartphone to mobile or wireless networks.
Network Connectivity
Having good mobile phone security awareness includes knowing how many wireless networks has your Smartphone been connected to over the course of its use.
Have a look and may be shocked at the number. Home broadband routers and public Wi-Fi networks in bars, restaurants or work could be listed, with the auto-connect option enabled.
This means every time your device 'senses' the presence of these network, it will connect and make your Smartphone visible on that network, fur the duration of its connectivity.
Therefore, it is recommended you either forget the network, so no future connectivity can take place, or switch off the auto connectivity feature.
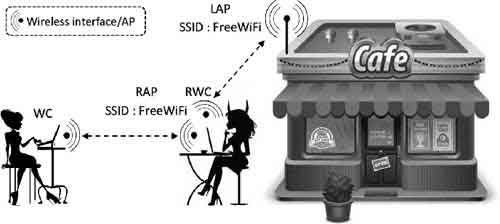
Public networks are prone to a relatively common technique called the evil twin attack. This is where the cyber criminal publishes their device as the public wireless network you are looking to connect to.
If you were to inadvertently connect to the cyber criminal's network, through their device, they could capture your various account login details and take your personal information such as photos and videos, for malicious use later, such as identity theft.
 Mobile Phone Security Awareness
Mobile Phone Security AwarenessEvil Twin Attack Explained
Source:- semanticscholar.org
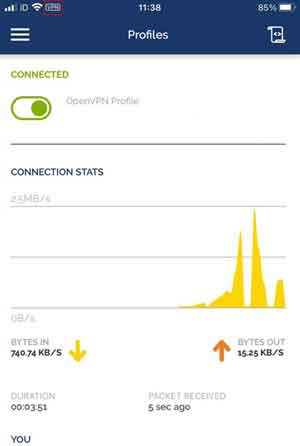
Another scam is called Wi-Fi spoofing, is similar to the evil twin attack. To help prevent against either, in addition to vigilance, is to set up a VPN solution on your device. Below is the VPN solution I have set up on my Apple iPhone.
 Mobile Phone Security Awareness
Mobile Phone Security AwarenessLive VPN Service on an Apple iPhone
Another form of wireless connectivity is Bluetooth. Despite its short range of approximately 10 metres, the effect is the same if your mobile phone is compromised. Busy bars, sporting events or festivals, for example, have many people in close-proximity.
Cyber criminals can access your phone remotely over Bluetooth and use it to make calls and use your data. This is known in the cybersecurity world as Bluesnarfing.
Set your Bluetooth discoverable setting to off. This is not a fail-safe method against all attacks. Disabling your Bluetooth service when not required is an added security step worth considering.
Remember, do not accept any request to connect or pair over Bluetooth from devices you do not recognize.
In the next section, we look at what you can do to protect yourself against malicious applications and data theft.
What Can Go Wrong With Applications?
The increase in mobile phone attacks are focused on the less secure android operating system. This attack increase can be attributed, in part, to the Triada mobile Trojan, which allows remote attackers to take control of your mobile phone, and is almost undetectable.
Infected applications are downloaded in their millions by unsuspected users, and for this reason alone, sensible steps such as antivirus, encryption and software patching, must be considered as part of your cybersecurity strategy.
Ensure to thoroughly check mobile apps before you commit to download from an App Store, especially from the Google Play Store. Although Google is making an effort to clean up the Play Store, lots of malware infected apps still exist.
For example, the kids gaming app, Crush Car, was reported by PCMag to have the HiddenAds Trojan embedded.
This form of malware is used to generate revenue by redirecting users to specific adverts that generate 'per-click-payments' when tapped or viewed.
 Mobile Phone Security Awareness
Mobile Phone Security AwarenessCrush Car App Reported containing Adware
Jailbreaking and rooting of Apple and Android mobile phones, respectively, are methods that remove the manufacturer's mandated security protocols. Consequently, it gives the user more control over how their phone is used, and what apps they can install, and from where.
 Mobile Phone Security Awareness
Mobile Phone Security AwarenessApple iPhone Jailbreaking In Progress
Source:- lifehacker.com.au
Unapproved Apps, that are not available in the Google Play Store and the Apple App Store, could now be installed. These Apps have an appeal, for example, as they are written to suppress inbuilt Ads that are part of that authenticate App.
Whilst this sounds great, be aware that these apps can also include hidden malware, and Jailbroken or rooted mobile phones are by default less secure.
Many years ago, I rooted an end of life android device that I didn't need any more. The process was cumbersome, and ended up killing the phone's performance.
Make sure when you install any Apps that you keep an eye on your accounts for unfamiliar charges and costs. If you see any relating to new Apps, take immediate action.
In addition, when updated apps are released, make sure they are applied as swiftly as you can. Updated apps often patch software vulnerabilities malware can exploit.
Remember to make sure you check the permission setting for all installed Apps, particularly that the App is accessing.
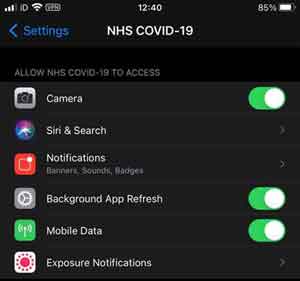 Mobile Phone Security Awareness
Mobile Phone Security AwarenessNHS Covid-19 Permissions Example
Protecting Your Personal Information
Malware often holds your personal data to ransom. To ensure you do not lose any of your personal information, make sure you have a good, robust backup process in place.
Also protect against a lost or stolen device by having an app or feature such as find my iPhone service enabled. This enables you to locate your device, remotely lock and even wipe it so no one can get hold of your data.
On android devices, make sure you install a good quality antivirus program, or make full use of any preinstalled antivirus products shipped with your manufacturer's hardware.
In addition, ensure you encrypt all of your files and folders, whether they are stored locally, or in the cloud.
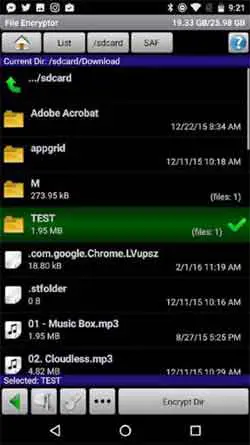 Mobile Phone Security Awareness
Mobile Phone Security AwarenessFile Encryption App In Action
Source:- techrepublic.com
Note that Apple holds the decryption key to your data that is stored in their iCloud service, or on your local device, and will hand it over to law enforcement if required.
In the final section of this article, we look at a selection of hints and tips for you to consider.
Mobile Phone Hints and Tips
Below is a simple of list of hints and tips for your consideration when securing your Smartphone. Have a look and see if any of the hint and tips improve your mobile phone security awareness.
- Android patching is critical, and not all suppliers issue patches. Make sure you check your supplier patching status before investing, and apply all available patches as swiftly as you can!
- Do not use the inbuilt save passwords facility. Invest in an encrypted product such as the McAfee App True Key solution.
- Enable multifactor authentication where possible
- Review and understand your device's inbuilt security features, and then set up to their maximum efficiency
- Secure your networking connectivity as detailed in this article
- Only use legitimate Apps, as detailed in this article, including the checking of their terms of use. If they want too much access to your data, don't install.
- Back up all of your data, as detailed in this article
- Install a well-known VPN solution, as detailed in this article
- Implement and an encryption tool on your android device if appropriate (some devices come with inbuilt security features)
- Enable the find my iPhone or install an equivalent app on your android device, including enabling features that protect your data by wiping if a certain number of incorrect passcodes are entered
- Implement a good passcode or pattern lock, as detailed in this article
- Regularly change your passcode and pattern lock
Mobile Phone Security Awareness | Final Thoughts
Smartphones are lost and stolen every day. How would you feel if your mobile phone was stolen? This reason alone should be motivation enough to improve your mobile phone security awareness.
Often it is the thought of spending time, bored, looking through settings to enable or disable, is the thing that puts people off. They prefer to get on with using the app.
However, there is a clear benefit in 'doing the boring stuff' first, as this will save you a lot of grief later on. If you are still unconvinced, I suggest you re-read this article, and the other article in this section.
